Important Shellshock Vulnerability Notice Regarding Your Website
Important Shellshock Vulnerability Notice Regarding Your Website: Ever wondered how a seemingly small bug can unravel your entire online presence? The Shellshock vulnerability (CVE-2014-6271 and CVE-2014-7169) is a prime example. This notorious flaw, discovered years ago, allowed attackers to remotely execute code on vulnerable web servers, potentially giving them complete control. This post delves into the nitty-gritty of Shellshock, exploring how it works, how to identify vulnerabilities on your site, and, most importantly, how to secure it against future attacks.
Let’s dive in!
Shellshock exploited a flaw in how Unix-like systems (like those running many web servers) processed certain commands. Essentially, attackers could inject malicious code within seemingly harmless inputs, gaining unauthorized access and potentially causing significant damage. Imagine the chaos: data breaches, website defacement, and complete system compromise – all stemming from a single vulnerability. Understanding the mechanics of this vulnerability is the first step towards protecting your website.
Understanding the Shellshock Vulnerability
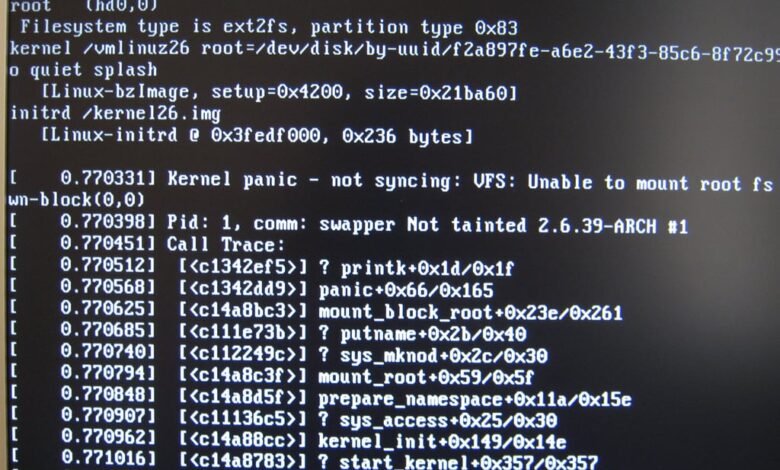
The Shellshock vulnerability, officially known as CVE-2014-6271 and CVE-2014-7169, was a critical security flaw affecting the Bash shell, a widely used command-line interpreter on Unix-like operating systems, including many web servers. Its impact was significant due to Bash’s prevalence and the ease with which it could be exploited to compromise systems. This vulnerability allowed attackers to execute arbitrary code remotely, potentially granting them complete control over affected servers.
Technical Details of Shellshock
The vulnerability stemmed from a flaw in how Bash handled environment variables. Specifically, functions defined within environment variables were improperly parsed. CVE-2014-6271 exploited a bug where Bash would execute code embedded within a function definition in an environment variable, even if that function was not explicitly called. CVE-2014-7169 extended the attack surface by showing that even simple variable assignments could trigger code execution under certain conditions.
Essentially, attackers could inject malicious code into an environment variable, and Bash would unwittingly execute it. This differed from previous vulnerabilities, as it didn’t require user interaction or specific commands; the simple act of receiving a specially crafted HTTP request could trigger the exploit.
Potential Impact on a Website
A successful Shellshock attack on a web server could have devastating consequences. Attackers could gain complete control of the server, potentially leading to data breaches, website defacement, denial-of-service attacks, and the installation of malware. They could steal sensitive information such as user credentials, credit card details, or intellectual property. Furthermore, the compromised server could be used as a launching point for further attacks against other systems.
Imagine a scenario where a popular e-commerce site falls victim – the consequences, including financial losses and reputational damage, would be substantial.
Unauthorized Access via Shellshock
The vulnerability allowed attackers to bypass security measures and gain unauthorized access by injecting malicious code into environment variables. This code could then be executed by the Bash shell, granting the attacker a shell on the server. This shell provides the attacker with the same level of access as the user running the Bash process, often the root user, granting them full control over the system.
The attack often involved crafting an HTTP request containing the malicious code within the HTTP headers. When the web server processed this request, Bash would execute the injected code, providing the attacker with remote code execution capabilities.
Examples of Exploitation Techniques
Attackers used various techniques to exploit Shellshock. A common method involved sending a specially crafted HTTP request containing malicious code within environment variables such as `HTTP_USER_AGENT` or `HTTP_COOKIE`. For example, a malicious request might look something like this (simplified for clarity, actual exploits were more complex):
`GET / HTTP/1.1\r\nHost: vulnerable.website.com\r\nUser-Agent: () :;; echo Content-Type: text/plain; echo; echo; /bin/ls -al\r\n`
This request would cause Bash to execute `/bin/ls -al`, listing the contents of the server’s directory. More sophisticated exploits could download and execute further malicious code, establishing a persistent backdoor on the server. The impact ranged from simple data exfiltration to complete server takeover, depending on the attacker’s goals and the system’s security posture. Numerous real-world examples demonstrated the widespread exploitation of this vulnerability shortly after its disclosure.
Assessing Website Vulnerability
Shellshock, a vulnerability affecting Bash, can pose a significant threat to websites that rely on CGI scripts or other Bash-based processes. Understanding how this vulnerability might affect your website is crucial for implementing effective mitigation strategies. This section details how to assess your website’s vulnerability to Shellshock exploits.
Potential Entry Points for Shellshock Exploits
Shellshock exploits typically target websites utilizing CGI scripts written in Bash or other scripting languages that rely on Bash as a processing engine. These scripts often process user-supplied data, creating an opportunity for attackers to inject malicious code. Another common entry point is through improperly configured web servers that allow the execution of arbitrary commands via environment variables.
For example, a poorly written CGI script might not properly sanitize user input before passing it to a Bash subprocess. An attacker could craft malicious input that triggers the vulnerability, potentially gaining unauthorized access to the server. Similarly, if a web server is configured to execute arbitrary commands based on environment variables, a Shellshock exploit could be used to bypass security measures.
Common Web Server Configurations Vulnerable to Shellshock
Web servers using CGI scripts written in Bash and not properly sanitizing user input are highly susceptible. Configurations that allow the execution of arbitrary commands based on environment variables without proper validation also present significant risk. Older versions of Apache, particularly those without appropriate security patches, are particularly vulnerable. A common scenario involves a web application using a CGI script that passes unsanitized user input directly to a Bash command.
The attacker could inject malicious code into the input, which would then be executed by the Bash interpreter with elevated privileges. This could lead to complete server compromise.
Steps to Perform a Vulnerability Scan for Shellshock
Before starting, it’s crucial to back up your website’s data and configuration. This precaution safeguards against accidental data loss or misconfiguration during the scanning process. A systematic approach is essential.
- Identify CGI Scripts and Bash-based Processes: Thoroughly examine your website’s codebase to identify all CGI scripts and processes that rely on Bash. This involves checking your server’s configuration files and directories where scripts are stored.
- Utilize Automated Vulnerability Scanners: Employ reputable vulnerability scanners specifically designed to detect Shellshock vulnerabilities. These tools can automate the process and identify potential weaknesses that manual inspection might miss. Many open-source and commercial options are available.
- Manual Testing (with caution): In a controlled testing environment, carefully test your identified CGI scripts and processes with known Shellshock exploit strings. This requires advanced knowledge and should only be performed by experienced security professionals in a safe, isolated environment to avoid accidental damage.
- Review Server Logs: Examine your web server’s access logs for any suspicious activity that might indicate a Shellshock exploit attempt. Look for unusual patterns or requests that don’t align with normal website traffic.
Checklist for Assessing Website Security Posture Regarding Shellshock
A comprehensive checklist helps ensure all aspects of your website’s security are addressed.
| Item | Status | Action Required |
|---|---|---|
| All CGI scripts and Bash processes identified | ||
| Vulnerability scanner employed | ||
| Server logs reviewed for suspicious activity | ||
| All identified vulnerabilities patched | ||
| Regular security audits scheduled | ||
| Employee training on secure coding practices implemented |
Mitigation Strategies
Shellshock, while a serious vulnerability, is entirely addressable through proactive measures. Understanding and implementing the right mitigation strategies is crucial for protecting your website and its data. This section Artikels practical steps to secure your web servers and applications against this threat.
Patching Vulnerable Web Servers and Scripts
The most effective way to mitigate the Shellshock vulnerability is to apply the necessary security patches released by your operating system and software vendors. This involves updating the Bash shell itself and any other affected components, such as CGI scripts or other applications that rely on Bash. These patches usually address the underlying code flaws that allow attackers to exploit the vulnerability.
For example, a vulnerable Apache web server running on a Debian system would require an update to the Debian packages containing Bash and any related Apache modules. Failure to patch leaves your systems open to exploitation.
Upgrading Outdated Software
Outdated software is a breeding ground for vulnerabilities, including Shellshock. Regularly updating all software components – operating systems, web servers, applications, and libraries – is paramount. Many vulnerabilities are discovered and patched over time, and using outdated software exposes your systems to known exploits. Consider implementing automated update mechanisms wherever possible to ensure that your systems are always running the latest secure versions.
This is especially important for applications directly interacting with user-provided data.
Securing Web Server Configurations
Beyond patching, secure web server configurations play a critical role in preventing Shellshock attacks. This involves restricting unnecessary access to the Bash shell. For example, disabling unnecessary CGI scripts or using alternative scripting languages that aren’t vulnerable to Shellshock can significantly reduce your attack surface. Additionally, implementing strict access control lists (ACLs) to limit who can execute scripts and what they can access is crucial.
Properly configuring your firewall to block unauthorized access attempts also adds a layer of protection.
Input Validation Techniques
Input validation is a crucial preventative measure. Never trust user-supplied input. Always sanitize and validate all data received from users before processing it. This involves checking the length, type, and format of the data to ensure it conforms to expected patterns. For example, if a script expects only numerical input, rejecting any alphanumeric input would prevent an attacker from injecting malicious code via environment variables.
Regular expressions can be particularly useful for implementing robust input validation. Consider using parameterized queries in database interactions to prevent SQL injection, which can be combined with Shellshock exploits.
| Strategy | Description | Implementation Steps | Potential Risks |
|---|---|---|---|
| Patching Vulnerable Systems | Applying security patches released by vendors to address Shellshock vulnerabilities in the Bash shell and related software. | Download and install the latest security updates for your operating system, web server, and any other relevant software. Reboot systems as necessary. Verify successful patching by checking version numbers. | System downtime during patching and reboot; potential incompatibility issues with older software; risk of incomplete patching if not carefully managed. |
| Software Upgrades | Updating outdated software to the latest versions, which often include security patches and vulnerability fixes. | Regularly check for updates from software vendors. Implement automated update mechanisms where possible. Thoroughly test upgrades in a staging environment before deploying to production. | Potential incompatibility issues; unexpected behavior from upgraded software; downtime during the upgrade process. |
| Secure Web Server Configuration | Restricting access to the Bash shell and implementing strong access control measures to minimize the attack surface. | Disable unnecessary CGI scripts. Use alternative scripting languages where possible. Implement strict ACLs to limit access to sensitive files and directories. Configure firewalls to block unauthorized access attempts. | Reduced functionality if certain scripts are disabled; potential for misconfiguration leading to security vulnerabilities; complexity in managing access control. |
| Input Validation | Sanitizing and validating all user-supplied input before processing to prevent malicious code injection. | Implement input validation using appropriate techniques, such as regular expressions and parameterized queries. Validate data type, length, and format. Escape or encode special characters. | Increased development time and complexity; potential for overlooking certain input patterns; risk of insufficient validation leading to vulnerabilities. |
Post-Exploitation Analysis (Hypothetical)

Source: slideplayer.com
Let’s explore the chilling scenario of a successful Shellshock exploit. Imagine an attacker has successfully leveraged the vulnerability. What happens next? The post-exploitation phase is where the real damage occurs, and the attacker’s actions can have devastating consequences for the website and its users.The attacker’s immediate goal after gaining initial access is to establish persistence and control. This allows them to maintain access even after the initial exploit window closes, potentially going unnoticed for extended periods.
They will strive to achieve complete control, exfiltrating sensitive data and potentially crippling the website’s functionality.
Persistence Mechanisms
Gaining persistence is crucial for any attacker. Several methods exist to achieve this after a successful Shellshock exploit. One common tactic is to create a backdoor. This could involve adding a user account with elevated privileges or modifying existing system scripts to include malicious code that allows remote access. The attacker might also create a cron job that executes their malicious script regularly, ensuring persistent access.
Another method involves modifying the system’s startup scripts, causing the malicious code to execute every time the system boots. These methods guarantee continued access, allowing for long-term exploitation and data exfiltration.
Data Breaches and System Compromises
The potential consequences of a successful Shellshock exploit are severe. Depending on the server’s configuration and the attacker’s skills, a wide range of sensitive data could be compromised. This could include user credentials, financial information, proprietary business data, intellectual property, and much more. Furthermore, the attacker might install additional malware, turning the compromised server into a launchpad for further attacks.
They could use the server for denial-of-service (DoS) attacks against other targets or to distribute spam. The compromise could also result in significant reputational damage and legal repercussions for the website owner.
Okay, so serious security alert: we’ve discovered a potential shellshock vulnerability on the site. While I’m working to patch that, I also wanted to share a fun project I’ve been working on – check out my guide on getting it on with youtube for better video optimization. Back to the shellshock issue: I’ll keep you updated on the progress of the fix.
Indicative Log Entries
Identifying a Shellshock attack requires careful examination of server logs. While there’s no single, definitive log entry, suspicious activity can provide strong indicators. For example, unusual commands executed via the vulnerable CGI scripts would be a red flag. Look for unexpected entries in the web server access logs, especially those originating from unusual IP addresses or containing unusual user-agent strings.
System logs might reveal the creation of new user accounts, modifications to cron jobs, or changes to system startup scripts. Anomalous network traffic, particularly outbound connections to unfamiliar IP addresses, should also raise suspicion. Examples of suspicious log entries might include:
`/usr/bin/env bash -c ‘…’` executed by user ‘nobody’
This entry shows the execution of a bash command, which is a classic sign of Shellshock exploitation. The user ‘nobody’ suggests that the attacker might have used the vulnerability to escalate privileges.
New user account ‘backdoor’ created.
The creation of a new user account with a suspicious name is a clear indication of an attempt to gain persistence.
Cron job added to execute ‘/tmp/malicious_script.sh’ every minute.
This shows the attacker has scheduled a malicious script to run repeatedly, ensuring continuous access to the system.
Security Awareness and Training: Important Shellshock Vulnerability Notice Regarding Your Website
The Shellshock vulnerability highlighted a critical need for robust security awareness training among website administrators. Understanding the vulnerability’s mechanics and potential impact is crucial for effective prevention and response. This section details a training module, a security awareness poster, examples of phishing emails, and the importance of regular security audits.
Training Module for Website Administrators
This training module aims to equip website administrators with the knowledge to identify, prevent, and respond to Shellshock-like vulnerabilities. The module would begin with an overview of the Shellshock vulnerability, explaining its technical details in a clear and concise manner, avoiding overly technical jargon. It would then cover the various ways Shellshock can be exploited, including through malicious scripts embedded in seemingly innocuous emails or websites.
A practical section would demonstrate how to identify vulnerable systems using readily available scanning tools, and finally, it would detail the steps necessary to patch and secure systems against this type of attack. The module would conclude with a series of realistic scenarios and quizzes to reinforce learning and assess understanding. Real-world examples of Shellshock exploitation, such as the 2014 widespread attacks, would be used to illustrate the potential consequences of neglecting security updates.
Security Awareness Poster
A visually appealing poster would communicate the Shellshock vulnerability’s essence in simple terms. The poster could feature a striking image, perhaps a cracked shell symbolizing the compromised system. The text would be concise and easily understandable, emphasizing the importance of regularly updating software and employing strong passwords. A key takeaway would be a clear call to action: “Update your systems now! Protect yourself from Shellshock.” The poster could also include a QR code linking to further information and resources, making it readily accessible to a wider audience.
This visual approach would complement the training module, reinforcing key concepts in a memorable and accessible format.
Examples of Phishing Emails Exploiting Shellshock
Phishing emails leveraging Shellshock might appear deceptively harmless. For example, an email could contain a seemingly innocuous attachment, like a “job application” or “invoice,” that actually contains a malicious script designed to exploit the vulnerability. Another tactic might involve embedding malicious code within the email’s HTML, automatically executing when the email is opened in a vulnerable system. The subject lines would likely be enticing, such as “Urgent Invoice,” “Job Offer,” or “Important System Update.” The email body would be crafted to appear legitimate, creating a sense of urgency to encourage the recipient to open the attachment or click a link.
These emails would exploit the user’s trust and lack of awareness regarding the Shellshock vulnerability.
Importance of Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are paramount in mitigating risks associated with Shellshock and other vulnerabilities. These assessments provide a systematic evaluation of a website’s security posture, identifying potential weaknesses before they can be exploited. Regular audits allow for proactive patching and configuration changes, minimizing the window of vulnerability. By conducting these assessments on a scheduled basis – for example, quarterly or annually, depending on the criticality of the website – organizations can significantly reduce their attack surface and improve their overall security.
Failure to conduct these assessments increases the likelihood of falling victim to attacks like Shellshock, resulting in data breaches, financial losses, and reputational damage. A documented and consistent approach to vulnerability management, including incident response planning, is crucial for effective mitigation.
Legal and Compliance Considerations
The Shellshock vulnerability, given its potential for widespread system compromise, carries significant legal and compliance implications for organizations. Failure to address this vulnerability can result in substantial financial penalties, reputational damage, and even legal action from affected parties. Understanding the relevant legal frameworks and compliance standards is crucial for mitigating risk and ensuring legal compliance.Ignoring a known vulnerability like Shellshock demonstrates a lack of due diligence and can expose your organization to liability for data breaches or other security incidents that result from exploitation.
This is particularly true if your organization handles sensitive personal information or financial data, as failure to protect this information can trigger legal action under various data protection laws.
Legal Ramifications of Failing to Address Shellshock
Failing to patch the Shellshock vulnerability can lead to several legal repercussions, depending on the jurisdiction and the nature of the breach. Organizations may face lawsuits from affected customers, partners, or employees for damages resulting from data breaches, service disruptions, or reputational harm. Governmental regulatory bodies may also impose significant fines for non-compliance with data protection regulations and industry-specific standards.
For example, a company failing to protect customer credit card data due to an unpatched Shellshock vulnerability could face substantial penalties under the Payment Card Industry Data Security Standard (PCI DSS). In cases involving sensitive health information, HIPAA violations could lead to even more severe consequences. The severity of legal ramifications depends on factors such as the extent of the damage caused, the organization’s negligence, and the applicable laws.
A proactive approach, including regular vulnerability scanning and patching, is the best defense against legal liabilities.
Relevant Compliance Standards Impacted by Shellshock, Important shellshock vulnerability notice regarding your website
Several key compliance standards are directly impacted by the Shellshock vulnerability. PCI DSS, which mandates the protection of cardholder data, requires organizations to maintain a secure network and regularly update their systems to address known vulnerabilities. A Shellshock vulnerability, allowing unauthorized access to systems, would be a clear violation of these requirements. Similarly, HIPAA, the Health Insurance Portability and Accountability Act, requires organizations handling protected health information (PHI) to implement appropriate safeguards to protect the confidentiality, integrity, and availability of that data.
The vulnerability could compromise PHI, leading to serious HIPAA violations and substantial penalties. Other standards, such as the General Data Protection Regulation (GDPR) in Europe, also have implications; failure to adequately protect personal data due to unpatched vulnerabilities could result in hefty fines.
Steps to Comply with Regulations After a Shellshock Incident
Responding to a Shellshock incident requires a structured and documented approach to ensure compliance with relevant regulations. This involves immediate containment of the breach, followed by a thorough investigation to determine the extent of the compromise and affected systems. This investigation should include identifying the source of the attack, the data accessed, and the individuals or systems affected.
A detailed incident report should be compiled and shared with relevant stakeholders, including regulatory bodies if required. Next, remediation steps should be taken to secure affected systems and prevent future incidents, including patching the vulnerability, implementing stronger access controls, and enhancing monitoring capabilities. Finally, notification procedures should be followed as per relevant regulations, informing affected individuals and authorities as required.
Maintaining detailed records of all these steps is critical for demonstrating compliance during any subsequent investigation or audit.
Closing Summary
Source: themarysue.com
Securing your website from the Shellshock vulnerability (and other similar threats) requires a multi-pronged approach. Regular security audits, up-to-date software, and robust input validation are critical. While the Shellshock vulnerability might seem like a thing of the past, the lessons learned remain highly relevant. Proactive security measures are the best defense against future attacks, ensuring your website remains safe and secure.
Remember, prevention is always better than cure – and in the world of cybersecurity, this couldn’t be truer.
Query Resolution
What is the difference between CVE-2014-6271 and CVE-2014-7169?
Both are Shellshock vulnerabilities, but CVE-2014-7169 represents a more serious and broader impact, exploiting a different part of the Bash shell’s functionality than CVE-2014-6271.
How can I tell if my website is still vulnerable to Shellshock?
Use a vulnerability scanner specifically designed to detect Shellshock vulnerabilities. Many free and paid options are available. Check your server logs for suspicious activity as well.
What if I’ve already been attacked?
Immediately secure your server by patching, upgrading software, and changing all passwords. Perform a thorough forensic analysis to determine the extent of the breach and take necessary steps to recover and mitigate further damage. Consider legal counsel.
Are there any specific plugins or tools for WordPress to mitigate Shellshock?
While there aren’t specific Shellshock plugins, ensuring your WordPress installation and all plugins/themes are up-to-date is crucial. A strong web hosting provider will also handle server-side security updates.
